Cloud Security Under Attack: Linux Malware Evolves
Threat Actors Increasingly Target Cloud Infrastructure with Sophisticated Tools
A new report reveals a growing threat to cloud security as attackers increasingly leverage Linux-based malware to compromise cloud environments. Researchers predict a shift towards more complex exploits, adapting existing tools to target cloud infrastructure specifically.
Evolving Malware Families
Unit 42 researchers identified five key ELF-based malware families—NoodleRAT, Winnti, SSHdInjector, Pygmy Goat, and AcidPour—actively used in attacks against cloud systems. Each family has undergone significant code updates within the last year, demonstrating ongoing development and support by threat actors.
Exploitation Techniques
These malware strains employ techniques like dynamic linker hijacking, abusing the LD_PRELOAD environment variable to inject malicious code into legitimate processes and exploit vulnerabilities in containerized infrastructure. This allows attackers to establish persistence, maintain stealthy command and control, and exfiltrate data.
NoodleRAT: A Versatile Backdoor
NoodleRAT provides attackers with remote access, SOCKS proxy tunneling, encrypted communications, and the ability to schedule code execution. The Linux variant, while similar to other backdoors, is considered a distinct malware family. It has been linked to Chinese-speaking threat actors, including Rocke and those associated with the Cloud Snooper campaign, targeting entities across the Asia-Pacific region.
Winnti: Stealthy Persistence
The Winnti malware achieves persistence by exploiting the LD_PRELOAD environment variable, loading into memory without altering system binaries. It enables remote command execution, file exfiltration, and SOCKS5 proxying. The Linux variant is reportedly used by China-nexus threat actors like Starchy Taurus (aka Winnti Group and BARIUM) and Nuclear Taurus (aka Tumbleweed Typhoon, THORIUM, Bronze Vapor).
SSHdInjector: Compromising SSH Access
SSHdInjector injects malicious code into the SSH daemon (sshd), granting attackers persistent access and enabling credential theft, remote command execution, and data exfiltration. It’s been observed in use by Digging Taurus (aka Daggerfly, Evasive Panda), targeting cyberespionage-related entities.
Pygmy Goat: Exploiting Vulnerabilities
Pygmy Goat, initially discovered on Sophos XG firewall devices, targets Linux systems through rootkit functionality and exploits a vulnerability (CVE-2022-1040). It intercepts SSH communications and offers capabilities like remote shells and network packet capture, targeting government agencies and NGOs in the Asia-Pacific region.
AcidPour/AcidRain: Destructive Wipers
Linked to the Russian threat actor Razing Ursa (aka Sandworm, Voodoo Bear), AcidRain and AcidPour are destructive Linux wiper malware strains. AcidPour, compiled for x86 systems, can wipe data on storage arrays and network devices, posing a significant threat to unprotected cloud systems.
Rising Cloud-Based Attacks
Cloud-based alerts increased by an average of 388% in 2024, and 45% of organizations report a rise in advanced persistent threat (APT) attacks. According to a recent report by Check Point, cloud misconfigurations were involved in 74% of cloud security incidents in 2023. Check Point Cloud Misconfiguration Report 2024 This underscores the need for proactive threat hunting and robust security measures.
Palo Alto Networks Protection
Palo Alto Networks Cortex Cloud offers machine learning-based detection for Linux ELF files, achieving 92% accuracy in identifying malicious samples. The Cortex PowerShell and VBS Machine Learning module also effectively detects cloud-specific malicious scripts, identifying 67% of tested scripts as malicious or suspicious.
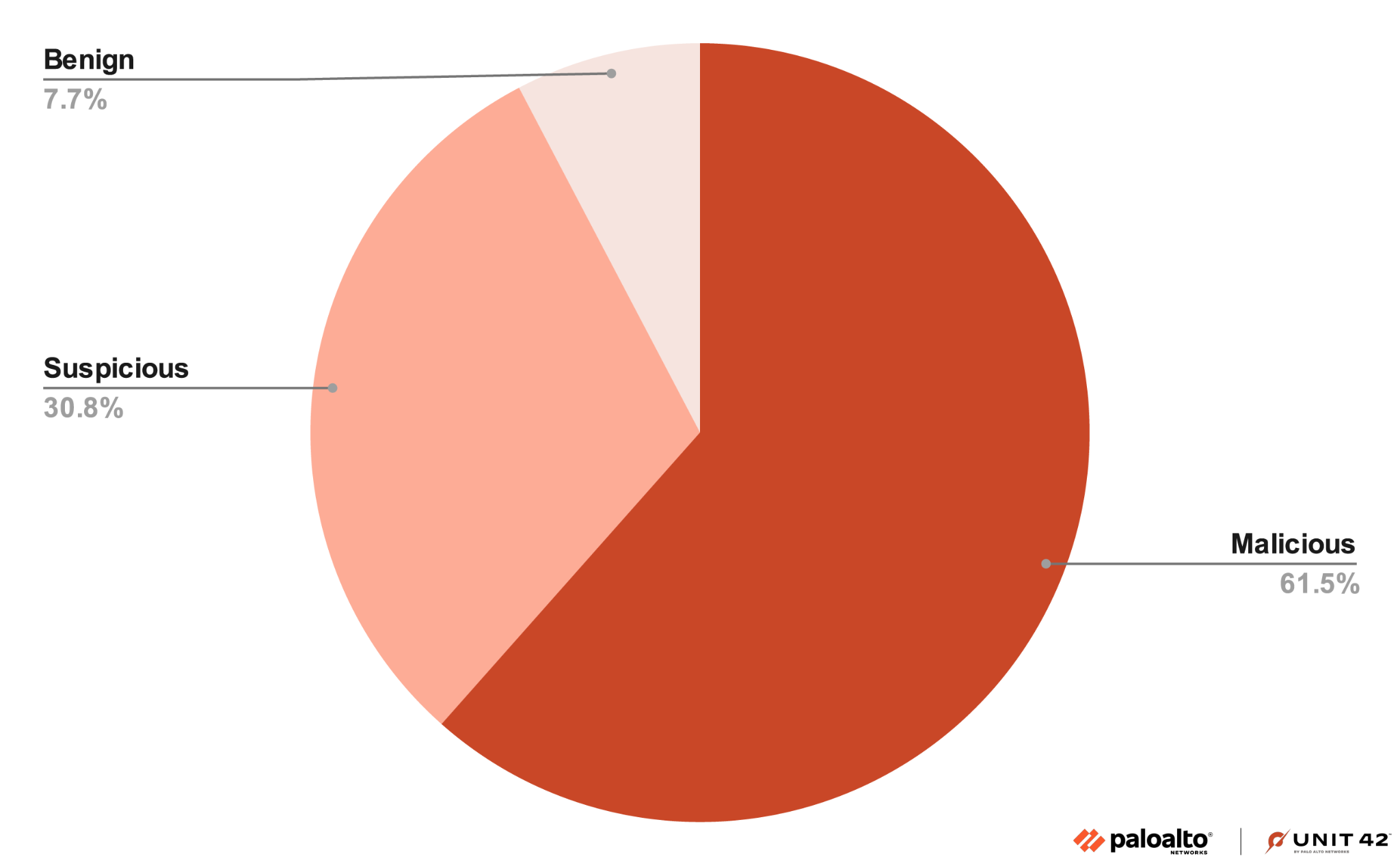
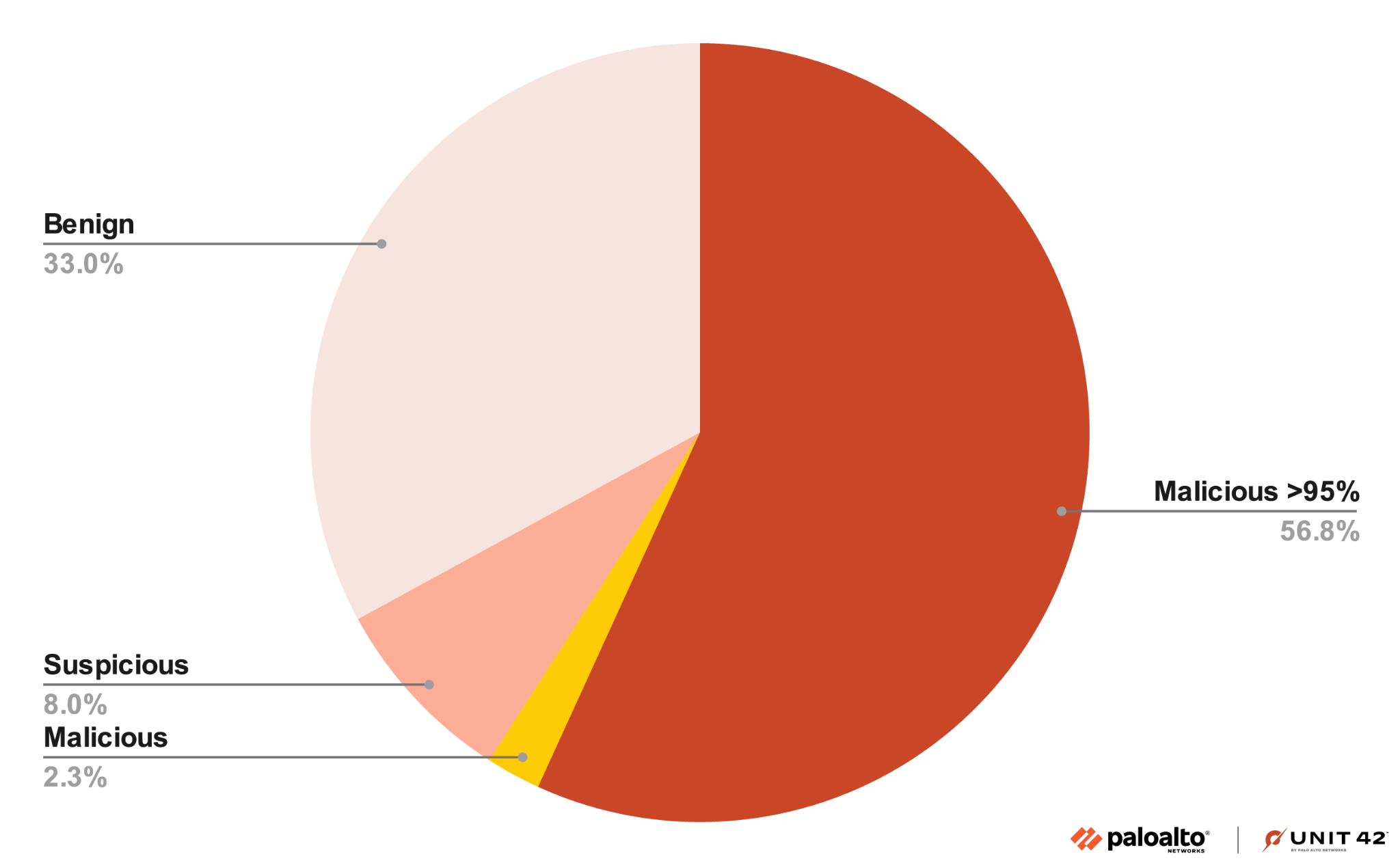
Defenders should implement endpoint security agents on cloud instances to detect malicious runtime processing and network traffic. Proactive threat hunting for ELF malware executions within cloud endpoints is crucial for maintaining a secure cloud environment.
If you believe you may have been compromised, contact the Unit 42 Incident Response team or call: North America: +1 (866) 486-4842, UK: +44.20.3743.3660, Europe and Middle East: +31.20.299.3130, Asia: +65.6983.8730, Japan: +81.50.1790.0200, Australia: +61.2.4062.7950, India: 00080005045107.

